Introduction
The winter holidays often transform our daily routines into a blend of family gatherings, last-minute shopping, and festive celebrations. During this period of cozy moments and social engagements, many people understandably shift their focus away from everyday concerns, including digital security. With attention directed toward holiday preparations and spending time with loved ones, it becomes surprisingly easy to lower one’s guard against potential threats.
As crypto holders redirect their attention toward family and holiday activities, malicious actors simultaneously increase their efforts, fully aware that reduced vigilance creates significant opportunities for theft and fraud. The holiday season represents a peak period for crypto scams and security breaches, making it essential to understand and implement practical protection measures. This comprehensive guide outlines effective strategies to reduce the risk of unauthorized access to cryptocurrency wallets during the holiday season and beyond. Let’s find out how to secure crypto wallet before the holiday season.
Key Takeaways
- Cryptocurrency holders should maintain hardware wallet security practices even during busy holiday periods, as reduced vigilance significantly increases the risk of unauthorized access to digital assets.
- Recovery phrases and seed phrases must be stored separately from hardware devices in secure locations that are physically inaccessible to unauthorized individuals.
- Every cryptocurrency transaction requires careful verification on your hardware wallet’s screen to prevent malware-induced errors and ensure transaction accuracy.
- Holiday travel and hectic schedules call for strategic cryptocurrency allocation, keeping only necessary amounts in accessible hot wallets while securing the majority of assets offline.
- Pre-holiday software updates to wallet applications, hardware wallet firmware, and operating systems create a protective barrier against emerging security threats and vulnerabilities.
Securing Your Hardware Wallet and Recovery Phrases
The foundation of crypto wallet security rests on two interconnected elements: the physical device itself and the recovery phrase that grants access to your funds. The comforting atmosphere of home, particularly when guests are present or when attention focuses on holiday preparations, can sometimes lead people to overlook these essential security measures. Understanding how to protect both components is crucial for maintaining control of your digital assets.
Hardware Wallet Physical Protection
If you use a hardware wallet, the first security step is straightforward yet frequently overlooked: keep it securely stored. Your device should be placed in a location where it cannot be easily accessed when not in use, even by people who may be visiting your home during the holiday season. This physical security prevents both casual mishandling and intentional theft. Whether you’re hosting family gatherings or traveling to visit relatives, ensuring your hardware wallet remains in a secure location demonstrates responsible asset management.
The challenge intensifies when you travel during the holidays. If you plan to carry your hardware wallet while visiting family or destinations, maintain the same security principles but with heightened awareness. Keep the device on your person or in a secure hotel safe rather than leaving it in common areas or unattended locations.
The Critical Importance of Recovery Phrases
While hardware wallet devices themselves deserve protection, the recovery phrase represents your ultimate security asset. Also known as a seed phrase, this collection of words functions as the master key to your cryptocurrency funds. According to Ledger’s recommended best practices for hardware wallet security, the optimal approach involves storing the hardware device separately from the recovery phrase to maximize resilience against theft or physical coercion. Ledger specifically advises that you should not keep your recovery sheet in a home safe, explaining that lacking immediate access to your backup substantially increases your resilience to physical threats.
This separation principle protects you in multiple scenarios. If your hardware wallet device becomes lost, damaged, or stolen while traveling or spending time away from home, the recovery phrase remains secure and allows you to regain complete access to your associated assets through another device. Without the recovery phrase, a stolen or damaged hardware wallet means permanent loss of funds. Conversely, if someone obtains only the recovery phrase without the hardware device, they cannot access your cryptocurrency because the device itself is required to authorize transactions.
Consider storing your recovery phrase in a physical location completely separate from your hardware wallet. Some security-conscious individuals use multiple storage methods, such as keeping one copy in a secure home safe and another in a safe deposit box at a financial institution. This redundancy ensures that even if one copy is lost or destroyed, you maintain access to your assets.
Verifying Every Transaction with Precision
With holiday shopping, cryptocurrency gifts, and end-of-year charitable giving, many crypto holders make more transfers than usual during this season. A core safety practice when sending cryptocurrency is to carefully verify the recipient’s address before confirming any transaction. This step protects you against a particularly insidious threat: malicious software that can replace a copied address with a different one without the user noticing the substitution.
Using Your Hardware Wallet Screen as a Trusted Confirmation Point
If you use a hardware wallet, it is critically important to physically verify the transaction details on the device’s screen itself, including the recipient address, the blockchain network, and the amount being sent. This verification step provides absolute certainty that the information displayed on your computer or phone has not been altered by malware or compromised software. Your hardware wallet’s screen serves as a trusted confirmation point because it operates independently from your potentially compromised computer or mobile device. You should approve only the transaction you intend to send, exactly as shown on the hardware wallet’s display.
This practice becomes especially important during the holidays when you might be making more transactions than usual. The temptation to process transfers quickly while managing holiday activities can lead to rushed decisions and skipped verification steps. Deliberately slowing down and carefully checking each transaction on your hardware wallet’s screen protects against this common error.
Updating Transfer Methods and Service Providers
Holiday gifts can create temptation to tap into long-term cryptocurrency savings or investments. If accessing these holdings involves a hardware wallet that has not been used in some time, exercising caution becomes particularly valuable. Rather than relying on past habits and remembered transfer methods, take time to recheck your service providers and current transfer procedures. Cryptocurrency exchanges, blockchain networks, and wallet providers occasionally update their processes or security protocols. Verifying current best practices rather than assuming unchanged procedures prevents potential errors or exposure to outdated security methods.
Recognizing and Preventing Phishing and Social Engineering Attacks
As sophisticated digital threats continue to evolve, phishing and social engineering tactics represent increasingly dangerous vectors for cryptocurrency theft during the holiday season. Understanding these threats and implementing defensive strategies is essential for protecting your assets.
The Surge in Holiday Crypto Scams
Lionsgate Network reported a substantial three hundred percent increase in holiday-related cryptocurrency scams during the 2025 holiday season, with fraudsters leveraging urgency, impersonation, and social engineering tactics across platforms including WhatsApp and Facebook. Scammers recognize that many people are busy, distracted, and more emotionally receptive during the holiday period, making them vulnerable to manipulation. These attackers may send fake emails or messages posing as established exchanges, wallet providers, cryptocurrency lotteries, or even friends offering so-called cryptocurrency gifts.
During the holiday season, scammers also intensify their use of fake online shopping websites and deceptive advertisements promising unrealistic deals, frequently requiring payment in cryptocurrency as the transaction method. According to a Federal Trade Commission alert, if a seller insists that payment can only be made using a gift card, wire transfer, payment app, or cryptocurrency, it represents a strong indicator of a scam. Legitimate retailers always provide multiple payment options and never demand cryptocurrency exclusively.
The Rising Threat of Deepfake Technology
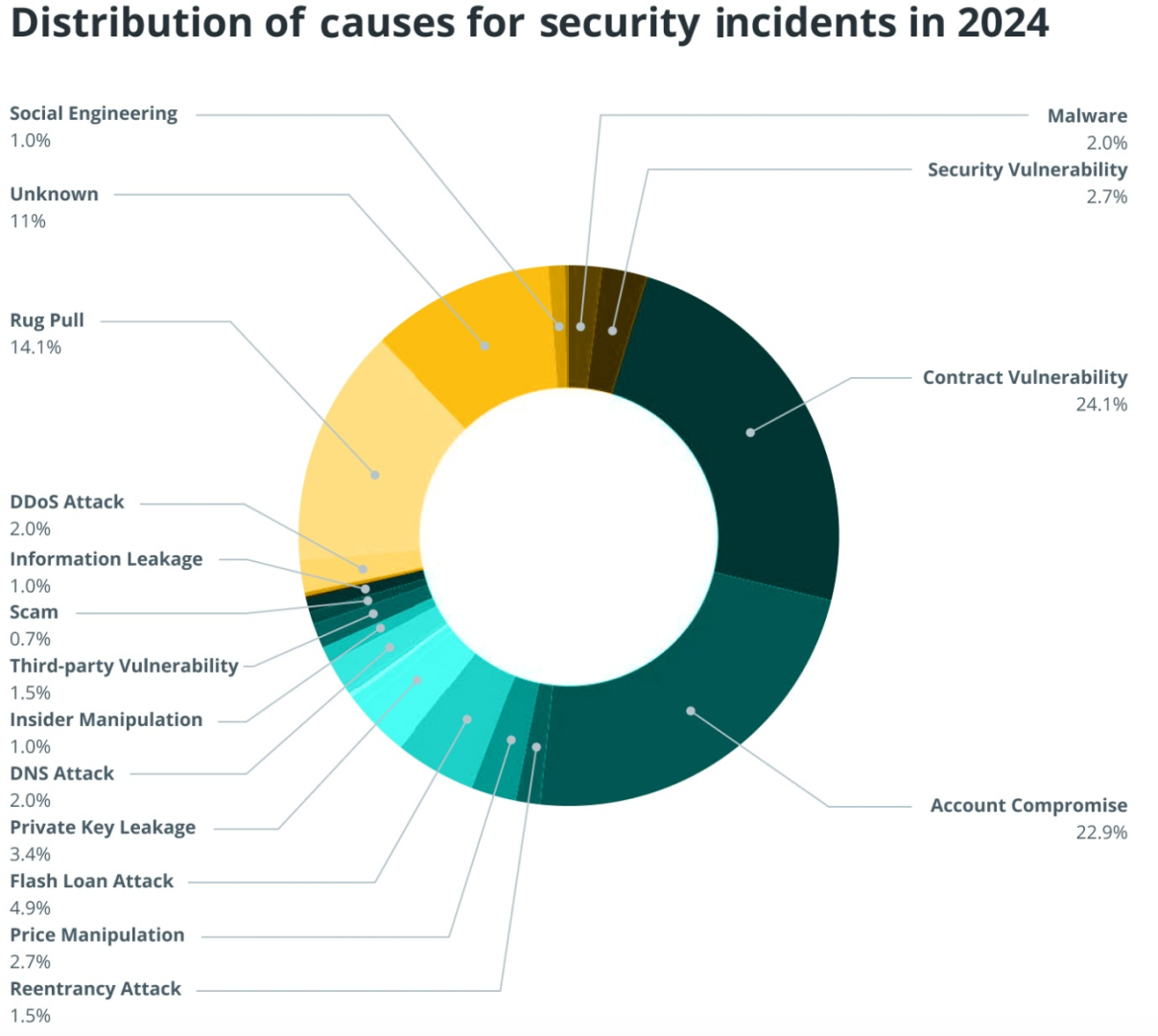
As artificial intelligence has advanced, scammers have gained access to increasingly sophisticated tools for executing fraud. Deepfake technology, which uses synthetic video and audio to convincingly impersonate trusted figures such as crypto executives or celebrities, represents an emerging and growing threat. According to research conducted by Bitget, SlowMist, and Elliptic, deepfake-driven schemes accounted for approximately forty percent of high-value cryptocurrency scams in 2024. This statistic underscores that deepfake fraud is not a theoretical risk but an active and substantial component of the current scam landscape.
These deepfake-based attacks leverage the natural human tendency to trust visual and audio confirmation. When a video appears to show a respected cryptocurrency figure or celebrity endorsing an investment opportunity, many people lower their skepticism and engage with the opportunity. The sophistication of modern deepfake technology makes these impersonations increasingly difficult to distinguish from authentic content.
Protecting Yourself from Phishing and Social Engineering
No legitimate wallet provider, exchange, or support team will ever ask for your recovery phrase or private keys. This principle represents an absolute rule without exceptions. Receiving an email, text message, or pop-up notification that urges you to enter this sensitive information online for an alleged urgent update or to claim a prize constitutes a strong indicator of a potential scam. Legitimate companies have no legitimate reason to request these secrets and will never ask for them through digital channels.
When evaluating suspicious communications, adopt a default posture of skepticism. If someone claims to represent your cryptocurrency service provider but the message creates urgency or requests sensitive information, contact the company directly using official contact information from their legitimate website rather than using contact details provided in the suspicious message. This verification step prevents you from inadvertently communicating with scammers impersonating legitimate entities.
Implementing Digital Minimalism During Holiday Travel and Busy Periods
A practical and effective method to reduce financial risk during busy travel periods or hectic social seasons involves adopting a form of strategic digital minimalism with your cryptocurrency holdings. This approach acknowledges the reality that travel and holiday periods increase the likelihood of device loss, theft, or compromise.
Strategic Asset Allocation for High-Risk Periods
If you are traveling during the holidays or anticipating particularly hectic weeks ahead, consider deliberately limiting the amount of cryptocurrency stored on devices you regularly carry, such as a mobile phone or laptop. This strategic reduction in accessible assets means that even if a device is lost or compromised while traveling, your losses remain limited to the smaller amount stored on that particular device.
Implement this strategy by keeping the majority of your cryptocurrency stored securely and offline in hardware wallets or cold storage solutions. Retain only a smaller, carefully calculated amount necessary for routine transactions or spending in a hot wallet that remains connected to the internet. This cautious and deliberate approach helps ensure that even if a travel device experiences loss or compromise, your core holdings remain protected and secure. The psychological benefit of knowing your major assets are safely offline can also reduce the stress and distraction that sometimes lead to poor security decisions.
Calculating Your Optimal Hold Amounts
Determining the right balance between accessibility and security depends on your specific travel plans and anticipated spending. Before the holidays begin, establish clear limits on how much cryptocurrency you need readily available for transactions. If you plan to make several crypto payments during your travels, estimate this amount generously and add a twenty percent buffer for unexpected needs. Place this amount in your hot wallet and keep the remainder securely offline.
Prioritizing Software Maintenance Before Holiday Season Peaks
The period immediately before the holidays represents an ideal time for proactive software maintenance across all your cryptocurrency-related systems. Taking action during this window ensures your maximum protection when activity peaks and your attention is most likely to be divided.
Updating Wallet Applications and Hardware Wallet Firmware
Wallet applications receive regular security updates that address newly discovered vulnerabilities and threats. Similarly, hardware wallet firmware updates provide essential security enhancements that protect against emerging attack vectors. Computer operating systems also require regular updates to maintain comprehensive security across your entire device ecosystem.
Schedule these updates well in advance of peak travel and social activity. By updating early, you avoid the scenario where critical security updates become available while you are traveling or managing holiday activities. If updates are pending when you are busy or traveling, the temptation to delay them increases significantly. Performing these updates before the holiday rush ensures your systems operate with maximum security protections already in place.
Creating a Pre-Holiday Maintenance Schedule
Develop a simple maintenance checklist for two weeks before your anticipated holiday travel or heaviest activity period. This checklist should include updating your wallet application, updating your hardware wallet firmware if applicable, updating your computer or mobile device operating system, and reviewing your recovery phrase storage location to ensure it remains secure. Working through this checklist methodically ensures you do not overlook critical security measures during the busy season ahead.
Fast Facts
- Holiday-related cryptocurrency scams increased by three hundred percent in 2025, with fraudsters primarily targeting busy and distracted individuals through social media platforms.
- Deepfake-driven cryptocurrency scams accounted for approximately forty percent of all high-value cryptocurrency thefts in 2024, demonstrating the sophistication and prevalence of artificial intelligence-enabled fraud.
- No legitimate cryptocurrency service provider will ever request your recovery phrase or private keys through email, text message, or any digital communication channel under any circumstances.
- Hardware wallet owners who experience device theft or damage can recover all their cryptocurrency holdings using the recovery phrase stored separately from the physical device.
- Individuals who limit cryptocurrency holdings on mobile devices during holiday travel can reduce maximum potential losses to a predetermined amount regardless of whether the device is lost or stolen.
Frequently Asked Questions
What should I do if I lose my hardware wallet during holiday travel?
If you lose your hardware wallet while traveling, do not panic about losing your cryptocurrency. As long as you have your recovery phrase stored safely in a separate location, you can recover complete access to all your funds. Order a replacement hardware wallet or use another compatible device, import your recovery phrase into the new device, and regain full access to your cryptocurrency holdings. The hardware wallet device itself is replaceable; the recovery phrase is irreplaceable.
How can I tell if an email claiming to be from my exchange is legitimate?
Legitimate exchanges never request your recovery phrase, private keys, or passwords through email or any digital communication method. If you receive an email asking for this information, it is definitely a scam regardless of how authentic it appears. Additionally, log into your exchange account directly using the official website or app to check for any legitimate notifications rather than clicking links in suspicious emails. You can also contact the exchange through official channels listed on their legitimate website to verify whether they sent the message.
Is it safe to use cryptocurrency while traveling during the holidays?
Yes, it is safe to use cryptocurrency while traveling if you follow essential security practices. The key is limiting the amount of cryptocurrency stored on devices you carry while traveling. Keep only a small amount necessary for planned transactions in a hot wallet on your phone or laptop, and store the majority of your holdings securely offline before you travel. This approach allows you to spend and receive cryptocurrency while traveling while protecting most of your assets from potential theft or device compromise.
Why should I update my wallet software before the holiday season?
Cryptocurrency wallet applications and hardware wallet firmware regularly receive security updates that address newly discovered vulnerabilities and threats. Updating before the holidays ensures your systems have maximum protection when you are busiest and least able to handle security incidents. If you delay updates until after the holidays when you have discovered a security breach or vulnerability, you have already exposed your wallet to potential attacks during the peak season.
Can someone access my cryptocurrency if they have my recovery phrase but not my hardware wallet?
In most cases, someone with only your recovery phrase cannot access your cryptocurrency if you use a hardware wallet that requires physical confirmation to approve transactions. However, they could import your recovery phrase into their own device and potentially access your funds, depending on whether your hardware wallet supports transaction signing on its own screen without internet connectivity. This is why protecting your recovery phrase with the same security you give to your hardware wallet is absolutely essential. Treat your recovery phrase as carefully as you would treat your cryptocurrency itself.
